Cyber threats are becoming more sophisticated by the day. Companies should know how to prevent, detect, and respond to these threats by performing a security and risk assessment. Penetration testing is one effective way to reduce the risk of cyber attacks.
What Is Penetration Testing?
Penetration testing and ethical hacking are two methods used to identify computer, network, or web application vulnerabilities.
Penetration tests specifically is performed to find the weak spots an attacker could exploit through a simulated attack. The pen test report can be used to fine-tune an organization’s security processes and controls.
Different Types of Penetration Tests
- Application Penetration Testing
- Web Application Penetration Testing
- DevOps Penetration Testing
- Network Penetration Testing
- API Penetration Testing
- Mobile Penetration Testing
- Cloud Penetration Testing
- IoT Penetration Testing
- Red Teaming Tools
Best Penetration Testing Tools
Here are the top 5 penetration testing tools on the market today.
1. BreachLock

BreachLock is a global penetration testing company that combines the power of expert hackers and artificial intelligence to deliver a comprehensive penetration testing solution as a service (PTaaS). It is a human-led, AI-enabled, penetration testing platform that provides continuous vulnerability scanning and remediation guidance while offering superior security and high yields over traditional pen testers. BreachLock is the only full-stack penetration testing solution with 100% in-house certified penetration testers.
This powerful pen-testing solution helps organizations meet compliance goals and remediate vulnerabilities faster than ever before.
BreachLock is a global leader redefining cyber security resilience and security testing for all sizes of organizations, from global enterprises to startups to mid-sized businesses. Enterprise clients include companies such as Ernst & Young, DocuSign, and national government agencies. The company has earned recognition with industry awards and analyst recognition for its innovative approach to customer engagement.
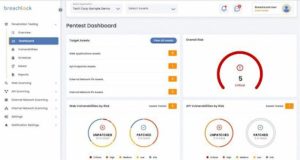
BreachLock is world-renown for leading the pen testing as a service (PTaaS) market with a purpose-built cloud platform engineered to test entire attack surfaces and full-stack environments. The PTaaS solution incorporates web applications, mobile apps, internal and external network protocols, APIs and other elements into a single security testing platform. This works ideally with DevSecOps teams and the Security Operations Center – when working together to minimize risks in the SDLC reduces the risk of a breach in production.
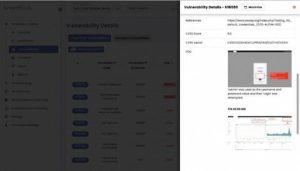
Key Features of BreachLock
- Guaranteed – Zero false positives
- 1-1 expert-guided remediation and customer service
- Manual and automated vulnerability discovery methods
- Monthly automatic scanning delivered with the BreachLock cloud platform
- Both online and offline penetration testing reports
- Automated retesting, patch validation, and continuous vulnerability scanning
- In-house, certified penetration testers, including CREST, OSCP, and OSCE-certified experts
- BreachLock is integrated with DevOps tools like JIRA, Slack, and Trello
- HIPAA, PCI DSS, SOC 2, ISO 27001, and GDPR-compliant
Pricing
This simple yet scalable penetration testing service provides a cost-effective annual subscription for on-demand pen testing. Users can choose between a one-time service or a continuous penetration testing service.
Visit the website of BreachLock to learn more about its world-class penetration testing tools and security validation solutions. Fill out the form on their website to schedule a demo or request a price quote.
2. Intruder

The intruder is an online penetration testing tool that performs security scans of servers, cloud systems, websites, and endpoint devices. It targets vulnerable configurations, missing patches, encryption weaknesses, application bugs such as SQL injection, cross-site scripting, OWASP top 10 vulnerabilities, and more.
The intruder has integrations with GitHub, Slack, JIRA, and Microsoft Azure.
Key Features of Intruder
- Automatically scan your system for new vulnerabilities
- Get alerts when exposed ports and tools change
- A holistic view of your security environment
- Compliance and reporting
Pricing
Intruder offers a 14-day free trial. It also provides three different pricing plans: The Essential plan, which costs $101/month; the Pro plan, which costs $163/month; and the Custom plan with tailored pricing.
3. Nessus

Nessus is a top penetration testing tool in the market. It is a cloud-based penetration testing solution that helps organizations secure their internet-connected attack surfaces. Nessus is fully portable and can be deployed on different platforms, such as Raspberry Pi.
In addition to its intuitive approach to navigation and user experience, Nessus provides a full suite of vulnerability scanning tools and tools.
Key Features of Nessus
- False positive rates are the lowest in the industry
- Dynamically compiled plugins to change code on demand
- Secure the infrastructure before deployment
- Pre-built and customizable templates
Pricing
Nessus offers a 7-day free trial, with two different pricing options:
- Nessus Expert, ideal for consultants and penetration testers;
- Nessus Premium, which is better suited for consultants and security practitioners.
4. w3af

w3af is a web application pen-testing solution for securing web applications. It can detect more than 200 vulnerabilities, such as SQL injection, cross-site scripting, and guessable credentials. Using custom HTTP requests, it attacks web applications and audits them.
In addition to its intuitive graphical user interface, W3AF also has a console user interface, where they can edit the security of their web applications in a few clicks.
Key Features of w3af
- Easy-to-use UI
- Python code base
- 200+ web application flaws for system identification
- Compatible with Linux, BSD, Mac, and Windows users
5. SQLmap

Another open-source penetration test tool is SQL, which automatically finds and exploits SQL injection flaws in databases. Penetration testing is supported, and a built-in detection engine with database fingerprinting is included.
Key Features of SQLmap
- Six different SQL injection techniques are supported: time-based blind, boolean-based blind, error-based, stacked queries, UNION query-based, and out-of-band injections
- Recognizing password hash formats automatically
- A range of database management systems are supported, including Microsoft SQL Server, MySQL, Oracle, IBM DB2, Amazon Redshift, and others
- Provides support for searching specific tables, databases, or columns across all databases
Who Provides the Best Pen Testing Tools?
The more we digitize our business processes, the more we get exposed to security vulnerability. Regular security assessments are necessary to avoid the cost of a successful cyber-attack. Penetration testing from BreachLock, for starters, can be an excellent option for discovering security vulnerabilities and providing remediation guidance. It uses a combination of manual, human-led testing, AI, and automation to come up with a revolutionary approach to cybersecurity.
This easy-to-use cloud platform delivers fast and accurate penetration testing tools. Launch your pen test within 24 hours and receive evidence-backed results within 7-10 business days. With BreachLock, organizations can mitigate security risks and maximize security outcomes.
Featured Image: Unsplash @ Sigmund
Read more investing news on PressReach.com.Subscribe to the PressReach RSS feeds:- Featured News RSS feed
- Investing News RSS feed
- Daily Press Releases RSS feed
- Trading Tips RSS feed
- Investing Videos RSS feed
Follow PressReach on Twitter
Follow PressReach on TikTok
Follow PressReach on Instagram
Subscribe to us on Youtube